November 1, 2023
Safeguarding Against the Rising Threat of SIM Swap Scams: A Comprehensive Guide
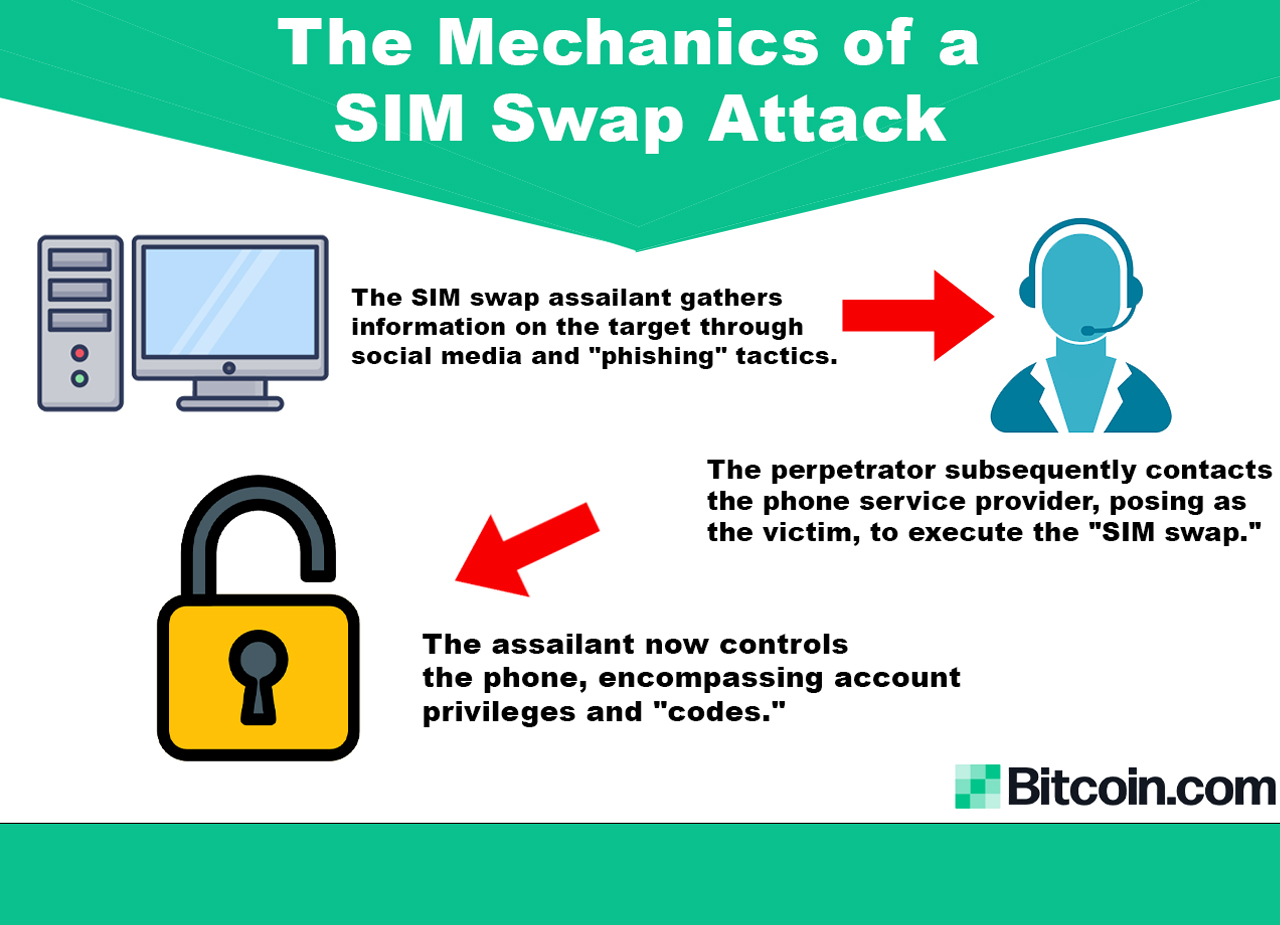
Introduction:
- In recent years, the SIM swap scam has emerged as a significant threat to individuals’ financial security. This fraudulent scheme exploits the connection between physical SIM cards and banking applications, providing scammers access to victims’ bank accounts and personal information.
SIM Swap Scam: An Overview:
Exploiting Technological Advances:
- The SIM swap scam takes advantage of the integration of banking applications with phone numbers, enabling the generation of OTPs (One-Time Passwords) and the receipt of critical bank-related messages.
Acquiring Personal Data:
- Scammers initiate their operation by collecting victims’ personal details, including phone numbers, bank account information, and addresses, often through phishing or vishing (voice phishing) techniques. Phishing involves sending malware-laden links through emails or messages to steal personal data.
Forging Victim Identity:
- Armed with the stolen data, fraudsters visit a mobile operator’s retail outlet, impersonating the victim with forged ID proof. They falsely report the theft of the victim’s SIM card and/or mobile phone, obtaining a duplicate SIM card. Notably, fraudsters can secure a duplicate SIM even if the original is still functional, directing all activation messages and information to themselves rather than the victim.
Why do victims receive Missed Calls?
Strategic Communication:
- In contrast to typical scams that involve tricking individuals into divulging OTPs and private data during phone calls, the SIM swap scam operates differently.
Distraction Tactic:
- Fraudsters initiate missed calls to their targets, prompting victims to check their phones and potentially ignore network connectivity issues.
SIM Exchange Execution:
- Perpetrators use these missed calls as a diversion while they execute the SIM swap. Once the SIM is swapped, fraudsters gain control over all calls and messages through the victim’s SIM, allowing them to initiate transactions unnoticed.
How do scammers withdraw money?
Phishing Information:
- After acquiring personal data through phishing attacks, scammers use this information to access bank portals and generate OTPs required for fund withdrawal.
OTP Access:
- Having control over the victim’s SIM card, fraudsters receive all OTPs, enabling them to authenticate transactions and steal money.
Data Sources:
- Accused individuals purchase data from hackers involved in data breaches or from online portals. Data breaches often involve private companies losing vast amounts of customer data. For instance, in April, Rentomojo, an electronics and furniture rental company, reported a data breach, acknowledging unauthorized access to customer data due to a cloud misconfiguration.
Arrests and Challenges:
Absence of Arrests:
- Delhi Police has not made any arrests related to the SIM swap scam. The accused effectively evaded capture by discarding duplicate SIMs and operating from multiple locations.
Cryptocurrency Conversion:
- Stolen funds are often converted into cryptocurrency, making tracking Bitcoin or other cryptocurrency transactions impossible due to encryption.
Protecting Yourself from SIM Swap Fraud:
Stay Vigilant:
- Be cautious of vishing or phishing attacks and avoid clicking on suspicious links or sharing sensitive information.
Don’t Ignore Missed Calls:
- Don’t ignore missed calls or switch off your phone, especially if you receive multiple missed calls. Contact your mobile operator immediately if such activity occurs.
Regularly Update Passwords:
- Change bank account passwords regularly for added security.
Set Up Alerts:
- Register for regular SMS and email alerts for banking transactions to stay informed.
Report Fraud:
- In case of fraud, promptly contact your bank authorities to block your account and prevent further fraud.
Conclusion:
- In an era where technological advancements bring convenience, they also open avenues for sophisticated scams like SIM swap fraud. Being aware of the tactics employed by scammers and following proactive steps to protect personal information and accounts is crucial in safeguarding one’s financial security. By staying vigilant and implementing preventive measures, individuals can significantly reduce the risk of falling victim to this pervasive threat.
September 24, 2025
September 23, 2025
September 22, 2025
September 17, 2025
